
TechCrunch recently reported on a mobile in-app ad fraud scheme that appears to have impacted over 200 Android apps that had been downloaded more than 150 million times.
Through ongoing support and detailed, in-depth fraud monitoring, Pixalate is able to provide additional data and context around the apparent scheme. Here’s a rundown of everything as it relates to the discovery.
According to TechCrunch, the malware, called SimBad, masqueraded as an ad serving platform and infected over 200 apps, “likely unbeknownst to the app developer.”
The malware “could install rogue apps, direct users to scam websites and show other apps in stores,” wrote TechCrunch.
SimBad was capable of running in the background of a mobile device without the user’s knowledge. The ultimate goal of the adware was to serve ads in the background and generate revenue.
The list of apps that appear to have been impacted — including app name, Bundle ID, and the number of installs (according to the Google Play Store) — can be found here.
Pixalate’s research team identified an additional 66 apps that appear to have been impacted by SimBad. These 66 apps were not on the original list when the apparent scheme was first uncovered.
You can find the 66 apps below. They have all been removed from the Google Play Store.
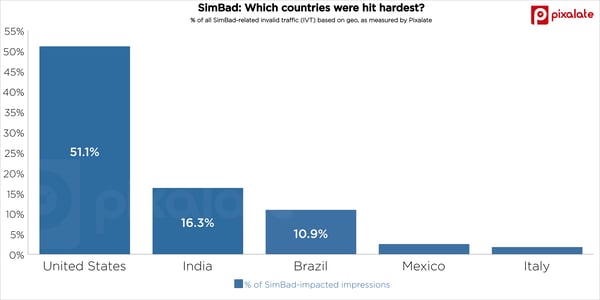
According to Pixalate’s data, over half (51.1%) of all SimBad-related invalid traffic (IVT) occurred in the United States. India (16.3%) and Brazil (10.9%) were the other most-impacted countries.
According to our data, over one-in-four (26%) of all SimBad-impacted impressions occurred on Samsung devices in the U.S. About 14% occurred on LG devices in the U.S., and 11% targeted Samsung devices in India.
Below are the top five devices (based on country) impacted by the SimBad scheme.
|
Device Brand |
Country |
% of all SimBad-impacted impressions |
|
Samsung |
United States |
26.18% |
|
LG |
United States |
13.87% |
|
Samsung |
India |
11.22% |
|
Samsung |
Brazil |
5.66% |
|
Zte |
United States |
3.32% |
Pixalate analyzed the permissions granted on the 200+ impacted apps. Here are the top 15 permissions all SimBad-impacted apps had in common:
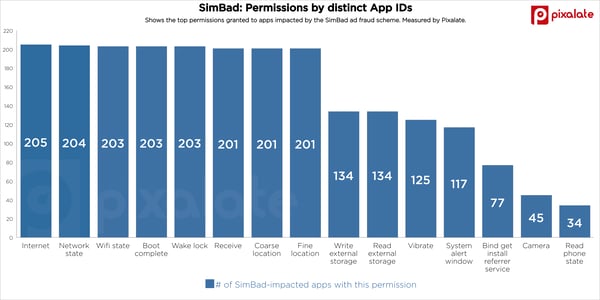
According to Pixalate’s data, 203 of the apps initially listed as part of the SimBad scheme had the ability to start when the user’s phone was turned on. The specific app permission to allow this is “android.permission.RECEIVE_BOOT_COMPLETED.”
This permission allows the app to know when the boot of the phone is complete. This is common in utility apps, but a lot of the apps impacted by the SimBad scheme were video games.
Additionally, 203 of the apps listed also had the permission “android.permission.WAKE_LOCK.” This permission allows for the app to prevent your phone from sleeping.
This may seem to be necessary permission for video gaming, but in the wrong hands, it can be used maliciously and can lead to battery drainage. By either creating (or targeting) apps that have this level of access to a user’s phone, fraudsters are essentially given a key to use the phone for behind-the-scenes ad fraud operations any time the device is on.
It’s important to remember that certain permissions — including the ones highlighted above — are not in and of themselves nefarious. However, some permissions are more attractive to fraudsters than others. With these permissions, scammers don’t have to rely on users to actually open an app or actively use their phone.
According to our data, over 28% of all SimBad-impacted impressions occurred when T-Mobile USA was the internet service provider (ISP). Jio, an Indian mobile network carrier, was the ISP for 14% of the impressions.
|
ISP |
% of all SimBad-impacted impressions |
|
T-Mobile USA |
28.39% |
|
Jio |
14.09% |
|
Spectrum |
7.74% |
|
Comcast Cable |
7.71% |
|
AT&T Wireless |
7.56% |
|
Verizon Wireless |
6.64% |
|
Sprint PCS |
5.90% |
|
Bharti Airtel |
4.76% |
|
AT&T U-verse |
3.20% |
|
Vivo |
3.05% |
In all, 38 unique ISPs were used, but the top 10 (shown above) accounted for nearly 90% of all impressions tied to the scheme.
The SimBad ad fraud discovery is yet another example of an attack specifically targeting mobile in-app advertisers. Need to do a better job protecting your budgets? Here are some of the key things for you to keep in mind moving forward.
The SimBad discovery, like MegaCast, is a reminder that mobile in-app’s ad fraud problem has not evaporated. Google says it removed about 700,000 apps from the Google Play Store in 2018, yet the ad fraud problem continues in 2019.
Ad fraud is routinely higher in the mobile in-app environment than anywhere else in the programmatic advertising ecosystem.
Our Q4 2018 ad fraud report reveals that mobile in-app invalid traffic (IVT) rates are 23%. Additionally, our data also shows that Android IVT rates are consistently higher than iOS.
Over 200 apps appear to have been impacted, many of which were game simulators. The apps had been downloaded a combined 150 million times, with one app — Snow Heavy Excavator Simulator — receiving over 10 million downloads.
The ‘Games’ app category was heavily targeted in this scheme, and as Pixalate research has revealed, the ‘Games’ category often has one of the highest IVT rates among Android app categories.
As much as 25% of Android in-app programmatic advertising goes to apps in the ‘Games’ category, which makes it highly appealing to fraudsters.
Want to make sure your business is protected from this type of threat?
The first step is to work with an MRC-accredited ad fraud solution. Pixalate has been accredited by the MRC in 17 metric areas, demonstrating its leadership in addressing today’s cross-platform risk challenges.
Pixalate offers the only system of coordinated solutions across display, app, video, and OTT for better detection and elimination of ad fraud. Speak with us today.
Disclaimer: The content of this blog reflects Pixalate’s opinions with respect to topics that Pixalate believes may be useful to the digital media industry. Any proprietary data shared in this posting is grounded in Pixalate’s proprietary technology and analytics, which Pixalate is continuously evaluating and updating. Pixalate’s opinions are just that – opinions – not facts or guarantees.
Per the MRC, “'Fraud' is not intended to represent fraud as defined in various laws, statutes and ordinances or as conventionally used in U.S. Court or other legal proceedings, but rather a custom definition strictly for advertising measurement purposes;” and also per the MRC, “'Invalid Traffic' is defined generally as traffic that does not meet certain ad serving quality or completeness criteria, or otherwise does not represent legitimate ad traffic that should be included in measurement counts. Among the reasons why ad traffic may be deemed invalid is it is a result of non-human traffic (spiders, bots, etc.), or activity designed to produce fraudulent traffic.”
*By entering your email address and clicking Subscribe, you are agreeing to our Terms of Use and Privacy Policy.
These Stories on Mobile
*By entering your email address and clicking Subscribe, you are agreeing to our Terms of Use and Privacy Policy.
Disclaimer: The content of this page reflects Pixalate’s opinions with respect to the factors that Pixalate believes can be useful to the digital media industry. Any proprietary data shared is grounded in Pixalate’s proprietary technology and analytics, which Pixalate is continuously evaluating and updating. Any references to outside sources should not be construed as endorsements. Pixalate’s opinions are just that - opinion, not facts or guarantees.
Per the MRC, “'Fraud' is not intended to represent fraud as defined in various laws, statutes and ordinances or as conventionally used in U.S. Court or other legal proceedings, but rather a custom definition strictly for advertising measurement purposes. Also per the MRC, “‘Invalid Traffic’ is defined generally as traffic that does not meet certain ad serving quality or completeness criteria, or otherwise does not represent legitimate ad traffic that should be included in measurement counts. Among the reasons why ad traffic may be deemed invalid is it is a result of non-human traffic (spiders, bots, etc.), or activity designed to produce fraudulent traffic.”

