Pixalate is an MRC-accredited company for the detection and filtration of Sophisticated Invalid Traffic ("SIVT") desktop and mobile web impressions.
According to the Media Rating Council’s (MRC) standards for Invalid Traffic Detection and Filtration Guidelines, there are two types of invalid traffic:
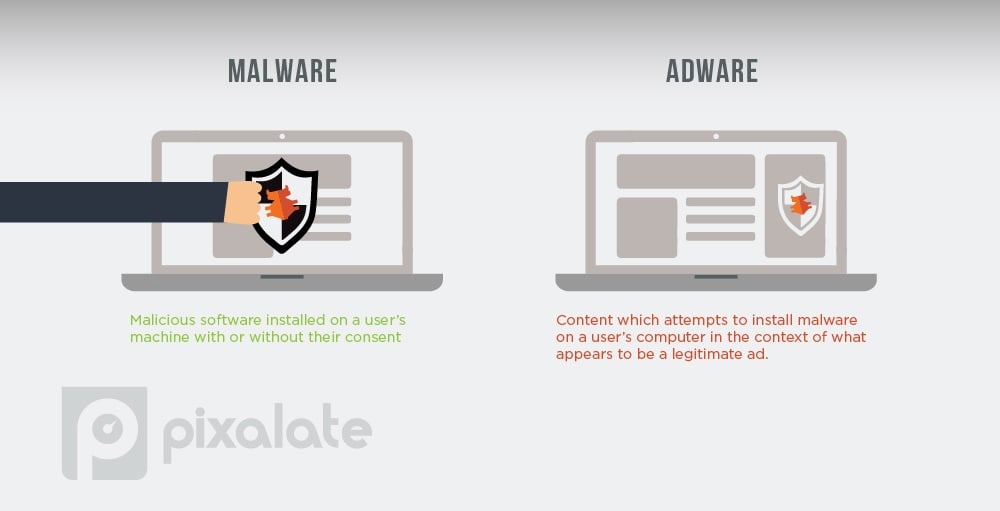
Two related examples of SIVT is “adware and malware.”
According to the MRC, adware and malware are considered SIVT.
Malware installed on a user’s computer can be used for a variety of nefarious means. In the advertising world, the malware can hijack the user’s computer and simulate legitimate activity to defraud advertisers.
An example of both adware and malware is the Chinese “Fireball” attack that infected over 250 million computers. The “Fireball” adware was also installing software (malware) on the infected computers, which hijacked the infected devices and simulated web traffic to generate and steal ad revenue.
MRC-accredited ad fraud detection and prevention companies must be able to identify and filter adware and malware.
Adware and malware are just two examples of Sophisticated Invalid Traffic (SIVT) as defined by the MRC. To learn about some of the other examples of SIVT, click on any of the examples below:
*By entering your email address and clicking Subscribe, you are agreeing to our Terms of Use and Privacy Policy.
These Stories on Thought Leadership
*By entering your email address and clicking Subscribe, you are agreeing to our Terms of Use and Privacy Policy.
Disclaimer: The content of this page reflects Pixalate’s opinions with respect to the factors that Pixalate believes can be useful to the digital media industry. Any proprietary data shared is grounded in Pixalate’s proprietary technology and analytics, which Pixalate is continuously evaluating and updating. Any references to outside sources should not be construed as endorsements. Pixalate’s opinions are just that - opinion, not facts or guarantees.
Per the MRC, “'Fraud' is not intended to represent fraud as defined in various laws, statutes and ordinances or as conventionally used in U.S. Court or other legal proceedings, but rather a custom definition strictly for advertising measurement purposes. Also per the MRC, “‘Invalid Traffic’ is defined generally as traffic that does not meet certain ad serving quality or completeness criteria, or otherwise does not represent legitimate ad traffic that should be included in measurement counts. Among the reasons why ad traffic may be deemed invalid is it is a result of non-human traffic (spiders, bots, etc.), or activity designed to produce fraudulent traffic.”

